Unfortunately, security incidents cannot be avoided – no matter how hard you try, something will always happen that will damage your information.
ISO 27001, a leading information security standard, requires you to record all the security incidents – but why is this needed, and what is the best way to do it? If you are looking for some helpful ISO 27001 incident managements tools, here is the answer.
ISO 27001 requirements regarding security incidents
ISO 27001 defines a security incident as an unwanted event that could endanger the confidentiality, integrity, or availability of information, whereas an event is any kind of technical occurrence or an activity that could indicate a possible breach of data.
The requirements of this standard for security incidents are numerous – according to section A.16 from ISO 27001, a company needs to:
- define responsibilities for handling incidents
- report all events and vulnerabilities that could turn into incidents
- set up a process of decision making on how to assess the events
- define the procedure for response to incidents
- learn from incidents, and thereby prevent future incidents from happening
- collect all the evidence that might be relevant for an incident
See this article to learn more: How to handle incidents according to ISO 27001 A.16.
What should an ISO 27001 incident management tool have?
When thinking about what kind of tool would be needed to handle incidents in compliance with ISO 27001, such tool should have the following characteristics:
- It should enable the definition of responsibilities through various policies and procedures, but also responsibilities for a particular incident.
- It should enable the recording of all events, vulnerabilities, and incidents, including all details for making an assessment and notification of responsible persons.
- It should enable the definition of a checklist of activities that need to be performed in order to resolve an incident, and notification of all persons regarding who needs to do what.
- It should be able to record all the details related to an incident, and enable the collaboration necessary to learn from the incident.
How does this look in practice?
Here’s how we implemented incident management in Conformio, a Software-as-a-Service tool focused on compliance with ISO 27001. During the ISO 27001 implementation, Conformio wizards will guide you in the creation of an Incident Management Procedure compliant with ISO 27001 requirements. Additionally, there is a folder called “Policies and Procedures,” where a company can upload all of its internal rules, including those related to incident management – such documents can be shared easily with other employees in the company:
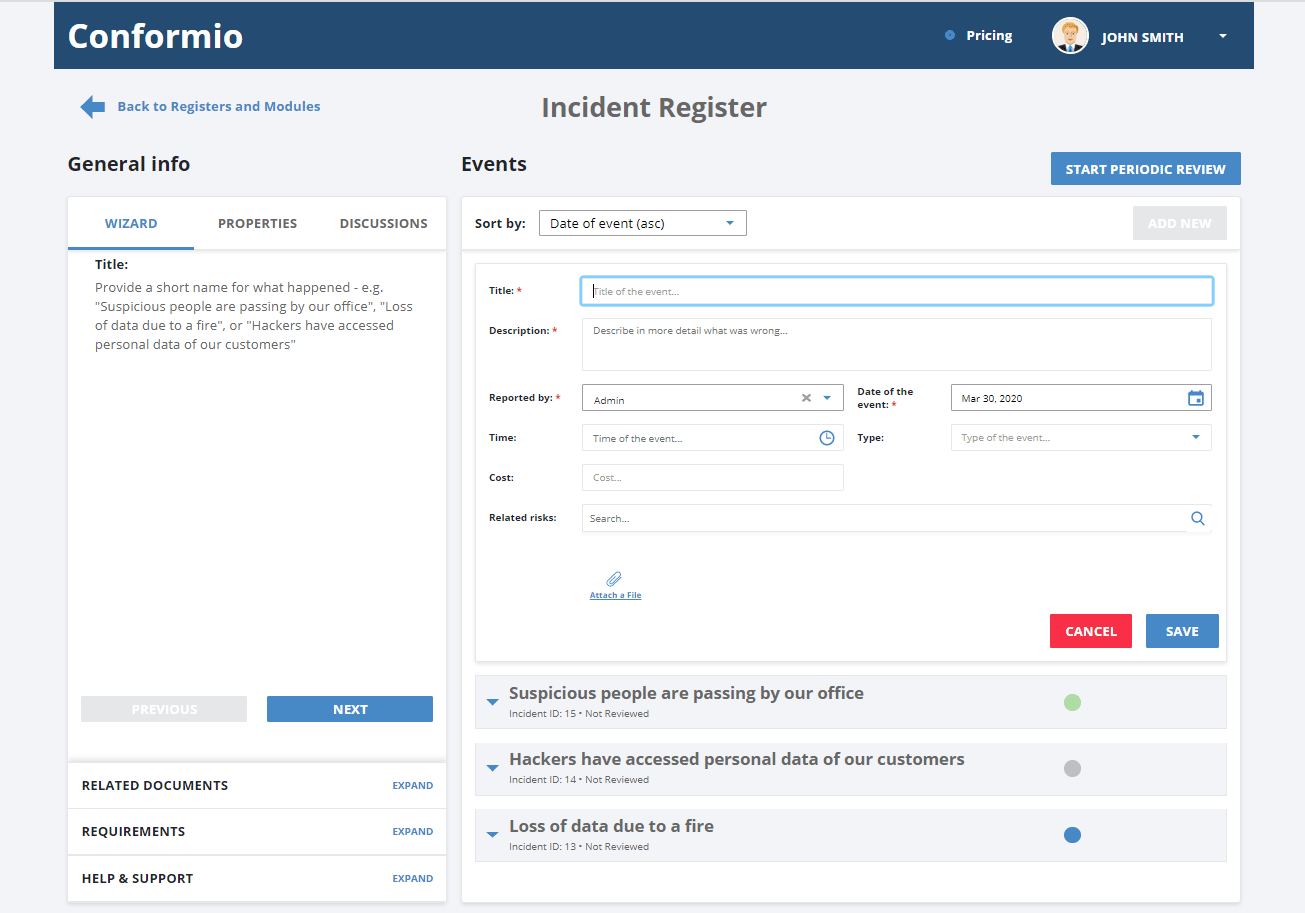
All incidents, as well as events and/or vulnerabilities, are recorded in the Incident Register – here’s what an overview of all the items looks like:
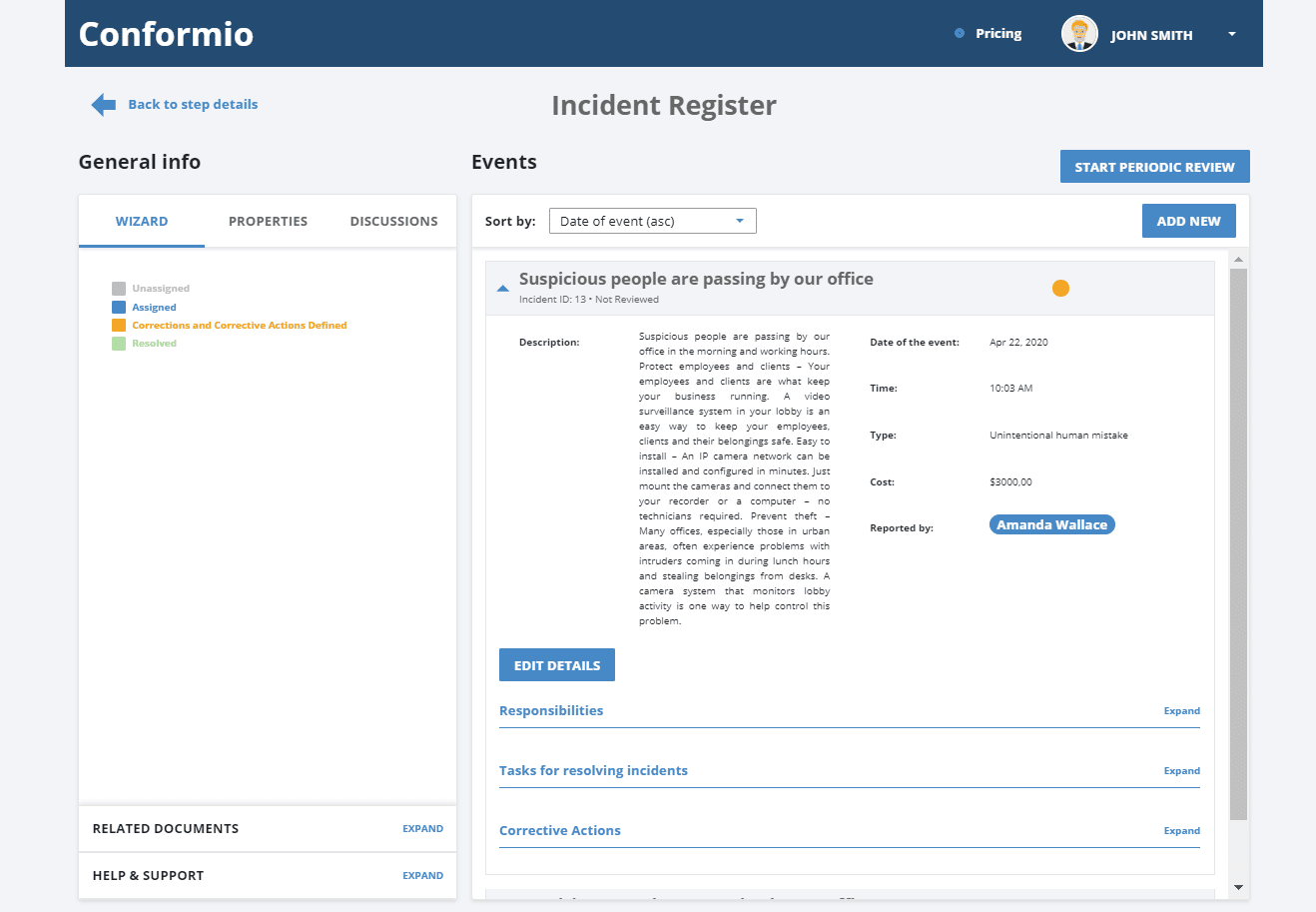
Once you open a particular item, then you can see various fields like status, date/time, type of incident, description, classification, related risks, etc.:
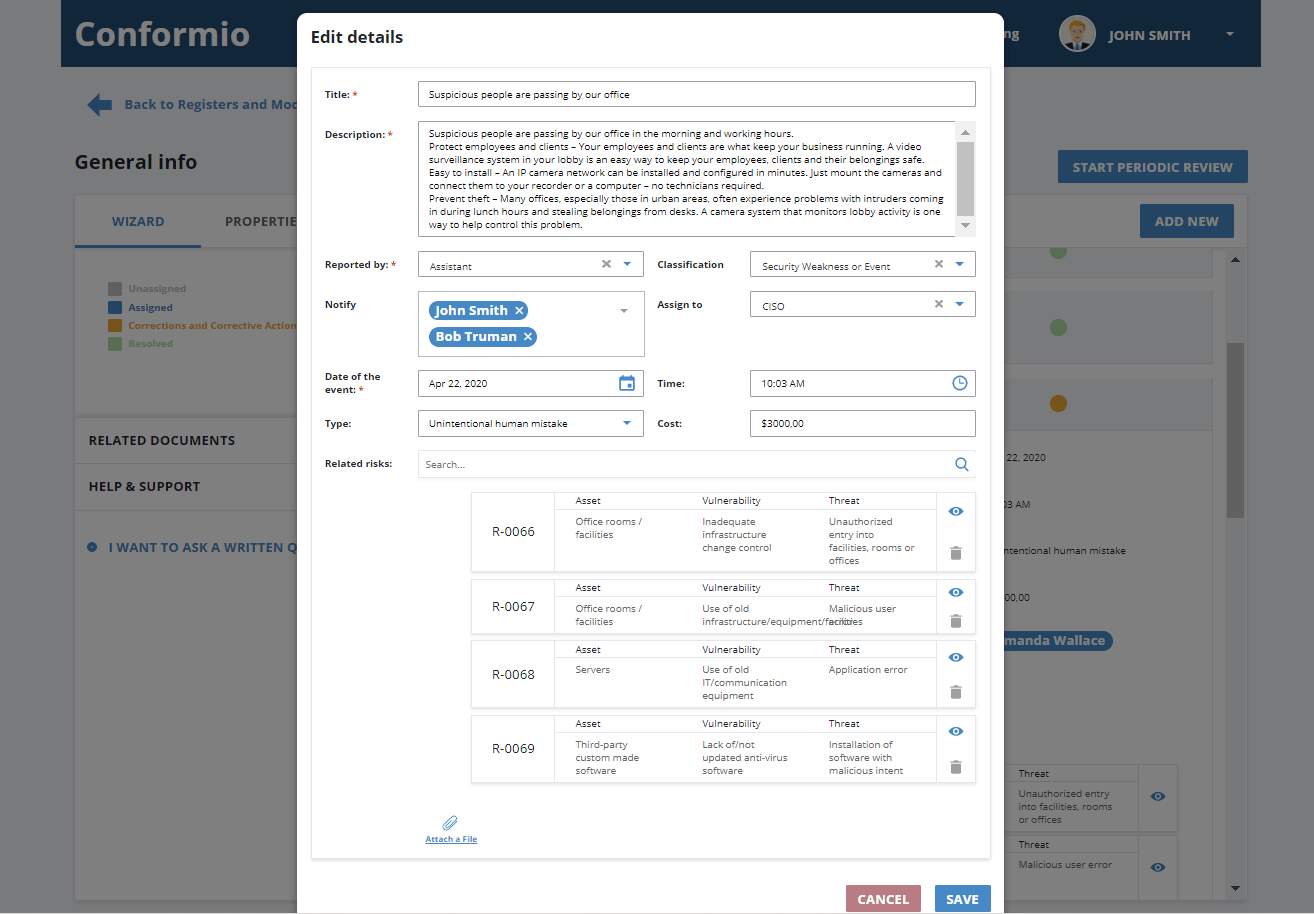
In the “assigned to” field, you can define who is responsible for the incident and which tasks need to be performed, and you can also communicate with members of your team; you can also upload the files with relevant analysis, add related risks, if any, and, in case you need something more systematic, you can define corrective actions, involving actions to fix incident impact, investigate and solve root causes, and perform disciplinary actions if needed:
Convenience of an online ISO 27001 incident management tool
Of course, you can do all of this using a combination of emails, internal documents stored on, e.g., Dropbox, records of events, vulnerabilities, and incidents stored in some help desk tool, defining tasks in a task management tool like Asana, collaborating through, e.g., Slack . . .
But you see where I’m going: why deal with such important issues through numerous tools? Incidents are enough trouble on their own, so handling them through one tool makes it at least a little bit easier.

 Rhand Leal
Rhand Leal