Investments in information security always present dilemmas: How much is enough? How do you justify implementing safeguard A instead of safeguard B? To help solve these dilemmas, some organizations assess information security risks that need to be treated, most of the time manually.
However, when the risk assessment process needs to provide a quick response, or needs to be performed many times in a short period, the manual and case-by-case approach may not be enough. In this article, we will show how ISO 27001 the leading ISO standard for information security management, helps implement systematic risk assessment, and how this process can be performed by software, using the Risk Management module of our ISO 27001 software solution, Conformio.
- Identify the risks with automatic suggestions for assets, threats, and vulnerabilities;
- Set task reminders for identified risks owners;
- Defined criteria for consequences and likelihood assessment are automatically displayed during risk assessment;
- Automatically calculate risks based on the defined method;
- Results of the risk assessment are automatically used to build the risk assessment report.
What is a security risk assessment in ISO 27001?
An ISO 27001 information security risk assessment is the process by which you identify, analyze, and evaluate information security risks, in order to prioritize them for treatment.
In short, the requirements to be fulfilled by this process, according to the standard, are:
- Define how to identify the risks that could cause a loss of confidentiality, integrity, and/or availability of your information.
- Define how to identify the risk owners.
- Define the criteria for assessing the consequences and the likelihood of the risk.
- Define how the risk will be calculated.
- Define the criteria for accepting risks and perform the risk assessment.
- Document the risk assessment process.
For further information, see: How to write ISO 27001 risk assessment methodology
What is a risk assessment tool?
A risk assessment tool helps you implement the risk assessment and treatment process in an automated way. You can choose between manual implementation of risk assessment or using a tool – both approaches are capable of fulfilling the ISO 27001 requirements.
For information security risk assessment, the most common approach, inherited from the previous 2005 version of ISO 27001, is the asset-based approach that lists assets with related threats and vulnerabilities. Although the 2013 version of ISO 27001 allows organizations to choose the approach that best fits their needs, the asset-threat-vulnerability approach remains the most-used one due to its ease of use.
How to manage risks with Conformio
Conformio is Advisera’s Software-as-a-Service solution for the implementation and operation of an ISO 27001-compliant ISMS, and for this purpose, its Information Security Risk Assessment module has these features to manage risks:
| ISO 27001 risk assessment requirement | Conformio’s features | Manual approach |
| Risk identification | Based on the asset-threat-vulnerability approach, a list of common assets, threats, and vulnerabilities is provided, together with automatic suggestions on which assets are related to which threats and vulnerabilities (see figure 1). You can customize the provided list by adding your own elements (see figure 2). | When using the asset-threat-vulnerability approach, a list of elements needs to be created first, and each time an asset is included in the risk register, the user needs to consult all available threats and vulnerabilities to identify proper correlations. |
| Risk owner identification | Task reminders for identified risks owners are automatically set up to warn them when related activities are required. | The risk assessment information needs to be consulted regularly to identify when a risk owner needs to take action. |
| Risk consequence and likelihood assessment | Criteria for consequences and likelihood assessment are defined during the customization of the risk assessment and risk treatment methodology document, and are displayed automatically during risk assessment. | The risk assessment and risk treatment methodology document needs to be consulted each time risk assessment is performed to identify how consequence and likelihood are defined. |
| Risk calculation | The method by which risk is calculated is defined during the customization of the risk assessment and risk treatment methodology document, and is calculated automatically during risk assessment once consequence and likelihood are entered. | Each risk needs to be calculated manually. |
| Risk acceptance | Acceptable risks, as well as risks that require treatment, are identified automatically in a visual way and are added to the risk treatment phase. | Unacceptable risks need to be identified manually and transferred to the risk treatment phase. |
| Document the risk assessment process | Results of the risk assessment are gathered automatically and used to build the risk assessment report. | Risk assessment and risk treatment information needs to be read, compiled, and copied to create the risk assessment report |
| Risk review | Task reminders for risk assessment review are defined during the customization of the risk assessment and risk treatment methodology document. | The risk assessment information needs to be consulted regularly to identify when a risk owner needs to take action. |
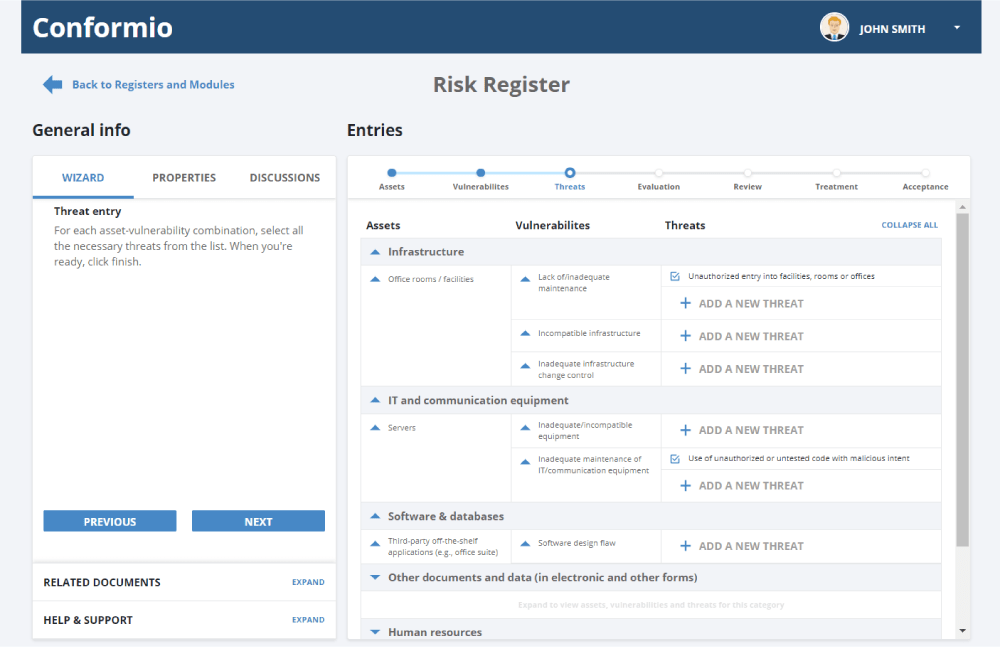
In figure 1 below, you can see what it looks like in Conformio when vulnerabilities are linked to assets, and available suggested threats are linked to them.
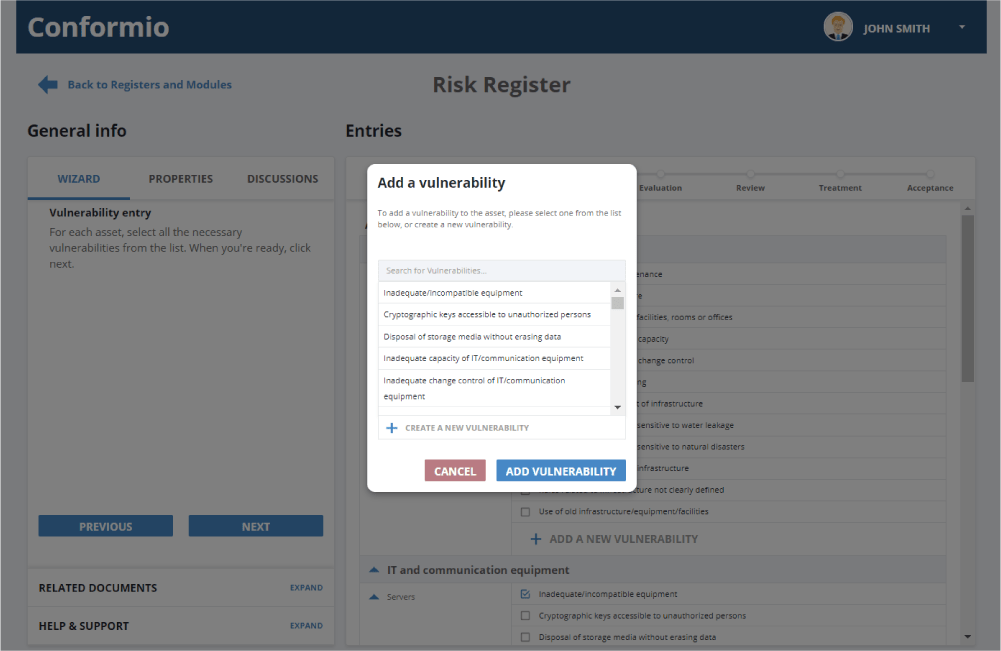
In the next figure, you can see what it looks like in Conformio when you want to add new vulnerabilities. There is already a list of suggested vulnerabilities related to the specific threats, and you can add vulnerabilities of your own.
Processes that can benefit from the use of risk assessment software
Risk assessment software can be very useful to quickly identify the need for some controls that can reduce risks, either by preventing incidents or reducing rework, such as:
- Screening (A.7.1.1) and Terms and conditions of employment (A.7.1.2) for the HR selection and hiring process
- Equipment siting and protection (A.11.2.1) and Equipment maintenance (A.11.2.4) for the maintenance process
- Separation of development, testing and operational environments (A.12.1.4) and Secure development policy (A.14.2.1) for the software development and maintenance process
- Management of technical vulnerabilities (A.12.6.1) and Restrictions on software Installation (A.12.6.2) for the ISO 27001 vulnerability management policy and the ISO 27001 vulnerability assessment process
- Change management (A.12.1.2) and Installation of software on operational systems (A.12.5.1) for the ISO 27001 patching policy and ISO 27001 patch management
Work faster and wiser using risk assessment software
Risk assessment is the core process of ISO 27001, because it helps prioritize where resources (e.g., money, equipment, personnel, etc.) should be allocated to ensure the most relevant risks are reduced to acceptable levels.
Information security risk assessment software like Conformio can help an organization not only to comply with the standard, but also to improve this process by automatically suggesting vulnerabilities and threats to identified assets, integrating information for SoA elaboration, automating repetitive tasks (e.g., remainders for risk review and controls performance measurement), and providing fast access to information for decision makers. And its integration with risk treatment makes it a complete risk management software solution.
To see how to use the ISO 27001 risk register with catalogs of assets, threats, and vulnerabilities, and get automated suggestions on how they are related, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Rhand Leal
Rhand Leal