Update 2022-04-08.
The content of an Information Security Policy is certainly one of the biggest myths related to ISO 27001 – very often, the purpose of this document is misunderstood, and in many cases, people tend to think they need to write everything about their security in this document.
Well, this is not what ISO 27001 requires. So, let’s see what this is all about. (See also: 5 greatest myths about ISO 27001)
- objectives: the general and specific objectives to be achieved by information security
- requirements section: reference to legal, statutory, and contractual requirements that must be fulfilled
- risk management: reference to the process to select the information security controls
- responsibilities: responsibilities for implementation, maintenance, and reporting of ISMS performance
- communication: to whom this policy needs to be communicated
- support: commitment with resources to implement and improve information security
What is the Information Security Policy according to ISO 27001?
The ISO 27001 Information Security Policy is a mandatory document used to define the leadership and commitment of an organization’s top management to the Information Security Management System (ISMS).
The purpose of Information Security Policy
In many cases the executives have no idea as to how information security can help their organization, so the main purpose of the policy is that the top management defines what it wants to achieve with information security.
The second purpose is to create a document that the executives will find easy to understand, and with which they will be able to control everything that is happening within the ISMS – they don’t need to know the details of, say, risk assessment, access control management, or backup copies, but they do need to know who is responsible for the ISMS, and what to expect from it.
What are the requirements for an ISO 27001 Information Security Policy?
ISO 27001 doesn’t say too much about the policy, but it does say the following:
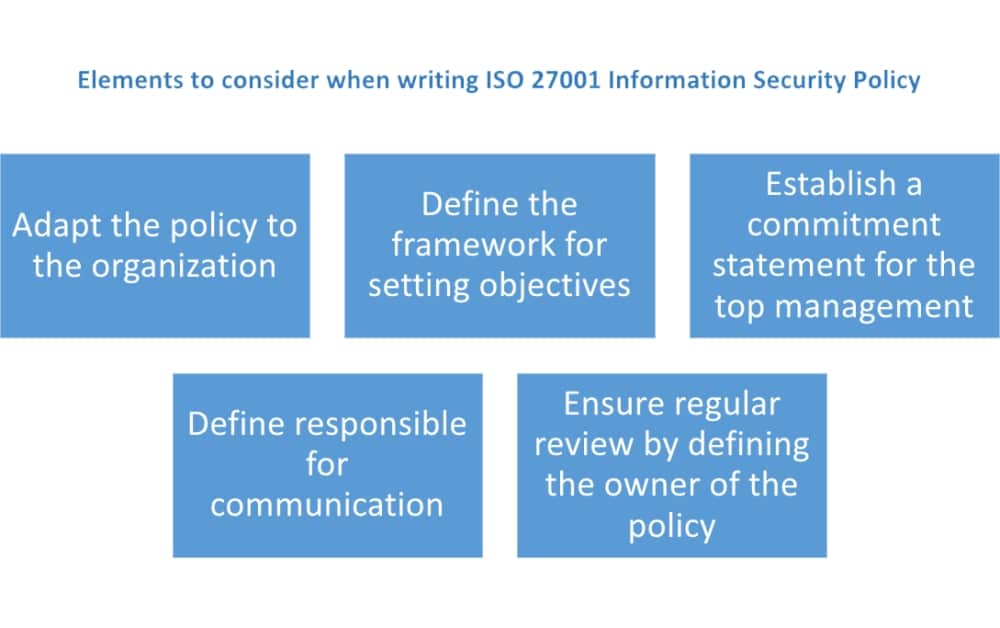
- The policy needs to be adapted to the organization – this means you cannot simply copy the policy from a large manufacturing company and use it in a small IT company.
- It needs to define the framework for setting information security objectives – basically, the policy needs to define how the objectives are proposed, how they are approved, and how they are reviewed. See also: ISO 27001 control objectives – Why are they important?
- The policy must show the commitment of top management to fulfill the requirements of all interested parties, and to continually improve the ISMS – this is normally done through a kind of a statement within the policy.
- The policy must be communicated within the company, but also – where appropriate – to interested parties (e.g., customer and suppliers); best practice is to define who is responsible for such communication, and then that person is responsible for doing it continuously.
- The policy must be regularly reviewed (e.g., annually) – the owner of the policy should be defined, and this person is responsible for keeping the policy up to date.
ISO 27001 information security framework to use in the policy
You can take a step forward from the ISO 27001 requirements, and define the basic ISO 27001 information security framework in your top-level Information Security Policy. The framework can include the following elements:
- objectives: the general and specific objectives to be achieved by information security
- requirements section: reference to legal, statutory, and contractual requirements that must be fulfilled
- risk management: reference to the process to select the information security controls
- responsibilities: responsibilities for implementation, maintenance, and reporting of ISMS performance
- communication: to whom this policy needs to be communicated
- support: commitment with resources to implement and improve information security
Although it is not mandatory, if you are a smaller company, you may also include the following (for larger companies, these issues are usually documented separately):
- The scope of the ISMS – this way the scope doesn’t have to exist as a separate document.
- Measurement – who will measure whether the information security objectives have been achieved, to whom the results need to be reported, how often, etc. (See also: How to perform monitoring and measurement in ISO 27001)
In some larger companies I’ve seen the Information Security Policy merge with the Enterprise Risk Management Policy. Although this is not wrong, I think it is better to keep these policies as separate documents – the focus remains much clearer.
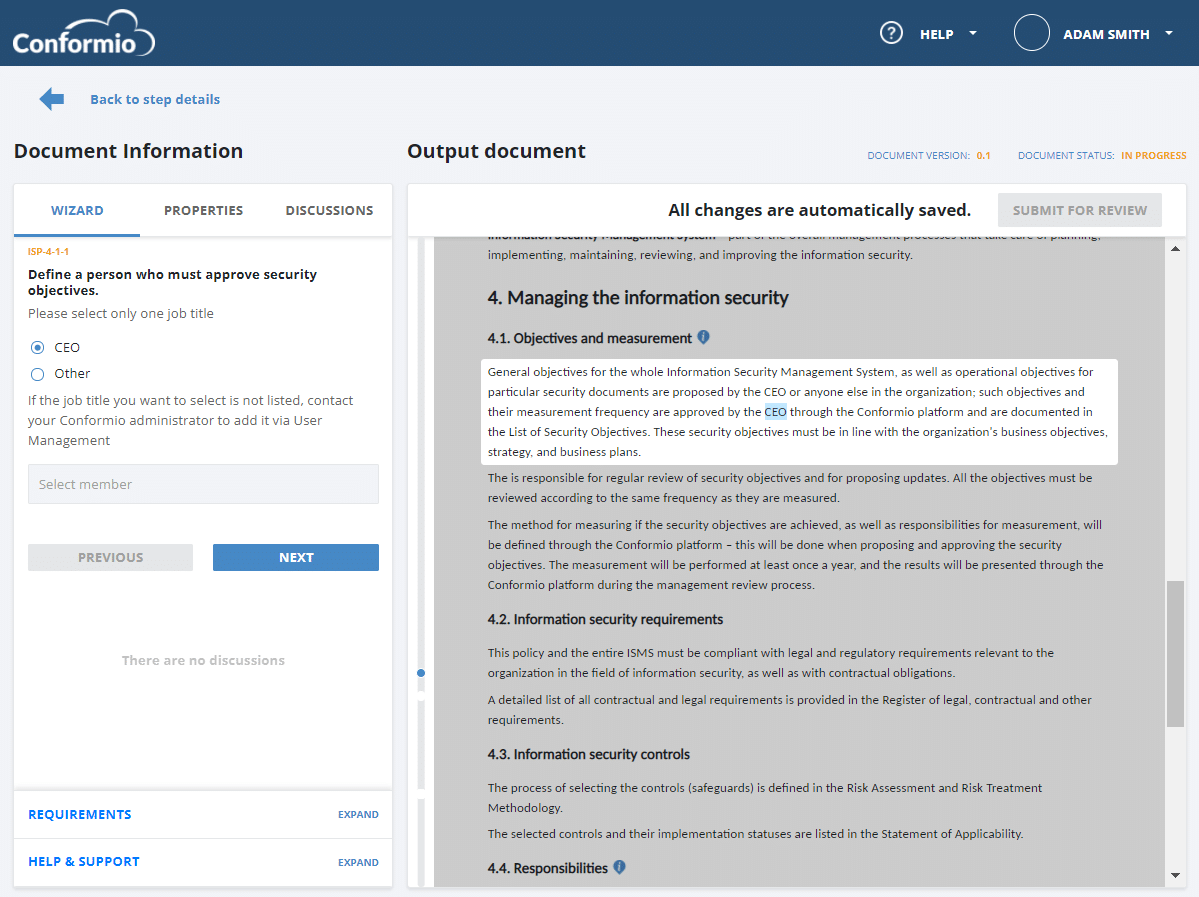
In the example below, see what filling out the Information Security Policy in your company could look like when guided with the help of Conformio document wizard, the leading ISO 27001 compliance software.
Inputs that are needed
There are a couple of inputs you have to take into account when writing the policy:
- Top management intentions with information security – the best thing would be to schedule an interview with your CEO and go through all the elements of the policy; you might send him an email a couple of days before the meeting, so that he has time to think about it.
- Legislation and contractual requirements – your policy should reflect those.
- Existing system for setting objectives – if such system exists, you should refer to it.
What is the role of security policies in ISO 27001?
As you saw in this article, the ISO 27001 Information Security Policy doesn’t have to be a very lengthy document. And no, you don’t have to include all the information security rules in this document. This will only make the document unnecessarily long and too complex to use and manage.
To cover all other information security rules that will guide and help your company protect information, you should develop detailed policies like Access Control Policy, Classification Policy, Acceptable Use Policy, etc. See also the article How to structure the documents for ISO 27001 Annex A controls.
Start looking at this policy in a different way
So the point is – the Information Security Policy should actually serve as a main link between your top management and your information security activities, especially because ISO 27001 requires the management to ensure that ISMS and its objectives are compatible with the strategic direction of the company (clause 5.2 of ISO 27001). Such top-level policy is probably the best way to do this.
So, you should keep this policy short and understandable for your top management. And please do not write lengthy documents of 80 pages trying to explain all the information security rules – this is the best way to create a document that no one will ever read.
To get the templates for all mandatory documents and the most common non-mandatory documents, along with the wizard that helps you fill out those templates, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Dejan Kosutic
Dejan Kosutic